Only other change to my Mac mini is I upgraded the primary hard drive to a 128GB SSD that was spare and disconnected the second (was a Mac mini server) as it was not needed and would just generate heat. Yes pfSense runs fine on Mac mini hardware. Sep 10, 2019 The answer is NO. MAC filtering is not a good method to prevent access to the internet. If the user is not at the level to change a MAC address then you can use a DHCP reservation for the IP address and block that at firewall level. Alternately set the machine on separate VLAN and block all traffic. Sep 17, 2020 There are three client options for Mac OS X.: The OpenVPN command line client. Most users prefer a graphical client, so this option will not be covered. Tunnelblick, a free option available for download at the Tunnelblick Website. Starting from version 2.4, pfSense supports 64-bit (amd64) exclusively while 32-bit (i386) support remains with pfSense 2.3, which will receive security updates for at least a year after pfSense 2.4.0-RELEASE. The amd64 platform works on current x86-64 hardware from Intel, AMD, etc.
In this article, we’ll configure On Demand VPN for iOS and macOS devices to connect to the VPN we created.
Jun 06, 2018 The version of pfSense used in this article is “version 2.4.3”. The version of MacOS used in this article is “version 10.13.4”. The following series of screenshots show the settings that i have used to allow a MacOS client to connect to the VPN.
Articles in This Series:
Part 1 – Certificate Configuration
Part 2 – VPN Configuration
Part 3 – Mobile Profile Configuration
Part 4 (Current Article)
Part 4 – On Demand VPN
So you want to get your hands dirty and force your VPN to connect based on network states? You’ve come to the right place! First and foremost, you’ll need an editor that handles XML. I recommend Atom.
Inspired by a Reddit post1, I began to look into Apple’s options for forcing VPN connections through the use of Mobile Configuration Profiles2. One resource I found that was helpful was this post from derman.com. So open up your Mobile Configuration file and let’s get to work!
Here’s the gist of it:
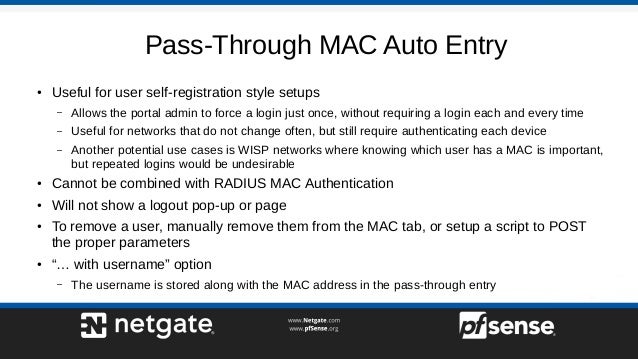
– You force connections through the use of conditions defined in the XML of the Mobile Configuration Profile.
- The matchine criteria can include any of the following:
- DNS Domain or DNS Server Settings (with Wildcard Matching)
- SSID
- Interface Type
- Reachable Server Detection
The type of matching you want to do is really up to personal preference. Below is an example of the very simple rules I use and where you want to place your own rules:
The most important part is the section that enables On Demand VPN:
The section that follows defines the rules you want to use. In my example, I only use two rules. Each <dict></dict> section defines one rule. Within each rule is an Action and at least one criteria. In my first rule, the action is to Disconnect when a URLStringProbe can contact a server of mine that is only accessible within my network. The final rule is the default action. This is very important. Per the Apple Developer Library, “Dictionaries are checked sequentially, beginning with the first dictionary in the array.” Therefore, if none of your rules match, you need a default to fall back on. In my case, if it can’t reach my internal server (is on the local network), then it should connect the VPN.
Below are some more examples of rules to give you a better idea of how they’re used.:
Disconnect when I have a specific DNS server and am connected to one of two specific wireless networks, otherwise connect (default):
Disconnect when I have a specific DNS server and am connected to any Ethernet connection, otherwise connect (default):
Disconnect when I am connected to any cellular connection, otherwise connect (default):
Connect when I am connected to any cellular connection and I can reach Google.com, otherwise disconnect (default):
Disconnect when I am connected to Ethernet and I can reach an internal URL, connect if I am on cellular, otherwise disconnect (default):
This should give you a decent idea of what is possible with manual editing of the Mobile Configuration Profile. Once you’ve set the parameters you want, save the file and follow Step 4 or 5 in Part 3 – Mobile Profile Configuration to add the profile to your mobile device.
References
PfSense VPN Client setup – Setting up an OpenVPN client to remotely access local network resources.
Now that we have a working OpenVPN server setup, we have to configure a VPN client on the machines that we will be using to remote into our network. Although we have VPN client options for many devices, including IOS and Android phones, we will be mainly focusing on Windows and Mac computers as they are traditionally used for work purposes.
Setup PfSense VPN Client
Navigate to the VPN tab within your PfSense menu bar, go to OpenVPN, and click on Clients. Click on the add button to add a new client, as shown below.
After clicking add, PfSense should take you to the OpenVPN Clients > Edit tab, here we will need to customize a few settings. We will provide a few examples of settings we had to change to accommodate our needs. However, your needs will vary.
Under the General Information tab, you can designate TCP/UDP connections for clients. We left it as IPv4 & UDP, for faster connections. In the “Server or Host” address section, please provide the IP address of your VPN Server.
- In a home network settings (this will be the dynamic/static IP address provided to you by your Internet Service Provider (ISP).
- In a work setting, this will be your VPN server’s network address reachable by the outside world.
You can also use a host-name for this purpose that resolves to a public IP address.
At the end of the form, please fill in a friendly description for easier administrative reference.
Next, we will fill out the “User Authentication Settings” field. Please be sure to use a secure username and password here for your clients.
Next, we will move on to configuring the “Cryptographic Settings” field. Here you want to add AES-128-GCM & AES-256-GCM under NCP algorithms if it isn’t already done for you.
Pfsense Openvpn For Mac
Under the Auth Digest Algorithm, choose SHA256(256-bit).
Under Hardware Crypto, you can add any supported hardware that your system has from the drop-down drop-down, or you can leave it disabled.

In the Advanced Config section, select IPv4 only or Both for gateway creation as shown below, then go ahead and click save.
You should now have a fully working VPN client configuration setup.
We will now go ahead and create a Client Export Package.
OpenVPN Client Export Package
We can create a client export package and send that file to our clients to install on their computers so that they can connect to our VPN server. PfSense has an effortless way to do this through the OpenVPN client export packager.
Go to System > Package Manager
Go to available packages as shown below, then search for OpenVPN & click install.
Click on confirm to finish the install process.
Below you will notice your package getting installed, and it should be done within a minute or less depending on the performance of your system.
Pfsense For Mac Pro

Pfsense For Mac Os
PfSense VPN User Manager
Now we need to add our users so that they can access our VPN Server. For this, go to PfSense System > User Manager, as shown below.
Fill out the fields as shown below, be sure to match all of the details including username and password that you set earlier in the VPN Client Config settings. Under Certificate Authority drop-down, be sure to choose your server certificate. Make sure the “click to create user certificate” button is checked. After these steps are completed, go ahead and click save.
You should now have a completed PfSense OpenVPN Server & a PfSense VPN Client Setup. You can now export these settings for your clients, as shown below.
Below you will see many options for client export. You can easily download a setup package for Mac OS or Windows, which includes the inline configurations, so you don’t have to import them separately.
Once the package is installed, you can download inline configurations for additional users and import them into the OpenVPN client utility.
The download options for inline configuration files or all-inclusive setup files are as follows.
Windows Downloads
Pfsense For Macbook
- Windows 7/8/8.1/2012R2
- Windows 10/2016/2019
Download Pfsense For Mac
Mac OS X Downloads
- Viscosity Bundle
Android/IOS
- Android (Download App for your device, then download the inline configurations from PfSense to import into the App)
- IOS (Download App for your device, then download the inline configurations from PfSense to import into the App)
Pfsense For Mac
If this article was informative in setting up a PfSense VPN Client, please be sure to give us a Like on our FaceBook page @ TechReally, it helps us know how we are doing. You can also join our Facebook Group @ Tech Really Facebook Group.